We are working to deliver immediate notification of a workaround to customers and a patch released by the end of the week.\u201d\n\n \n\n\nFound this article interesting? Parsing Information\")\r\n memory_address = 0\r\n ascii_string = \"\"\r\n for byte in read_bytes(host):\r\n \tascii_string = ascii_string + is_printable(byte)\r\n\tif memory_address%61 == 60:\r\n\t\tif ascii_string!=\".\":\r\n\t \t\tprint ascii_string\r\n\t \tascii_string = \"\"\r\n\tmemory_address = memory_address + 1\r\n\r\ndef check(host, port):\r\n print(\"[!] FIX-Fixed organization criteria in report Devices per remote server (PRB0042315). ]108:80\n * 45[.]80[.]149[. \n\n \n\n\n** Options: **\n\n \n\n\n\\--file Mandatory - File containing valid HTTP request and SQL injection point (SQLINJECT). FIX The agent installation date (ClientInstallDate) is updated when a newer agent is installed (04426066). NEW Help text is now available through the command line argument -h aligning with agents for other platforms (MacOS, Linux, and Windows). Enhancements-Microsoft Office 365:The connector now gathers additional user activity data. Bug fixes. The attackers even go so far as to offer to call the target user to walk them through clicking the link. [_Source_]()\n\nThe following [Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) ]()have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:\n\n### [**CVE-2022-37976**]()** | **Active Directory Certificate Services Elevation of Privilege (EoP) Vulnerability\n\nThis vulnerability has a CVSSv3.1 score of 8.8/10.\n\nPolicy Compliance Control IDs (CIDs):\n\n * **4079 **Status of the 'Active Directory Certificate Service' ** **\n * **14916 **Status of Windows Services** **\n * **24842** Status of the 'LegacyAuthenticationLevel' setting\n\n[Exploitability Assessment](): **_Exploitation Less Likely_**\n\n* * *\n\n### [CVE-2022-33645]()** | **Windows TCP/IP Driver Denial of Service (DoS) Vulnerability\n\nThis vulnerability has a CVSSv3.1 score of 7.5/10.\n\nPolicy Compliance Control IDs (CIDs):\n\n * **4842** Status of the 'Internet Protocol version 6 (IPv6) components' setting\n\n[Exploitability Assessment](): **_Exploitation Less Likely_**\n\n* * *\n\nThe following QQL will return a posture assessment for the CIDs for this Patch Tuesday:\n \n \n control:( id:`4079` OR id:`4842` OR id:`14916` OR id:`24842` ) \n\n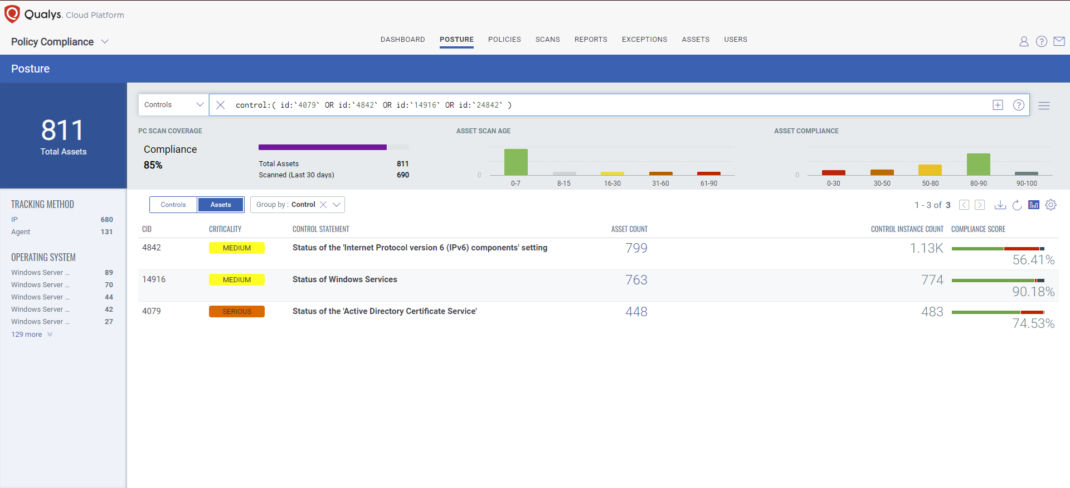\n\n! FIX The application store properties are now available in the Web Configurator import mappings table (PRB0043225). \n\nIn response to the breach, FireEye has provided Red Team tool countermeasures which are [available on GitHub](). More information about this functionality can be found in the docs-portal. (04536724), Fix Correction made when an error in the O365 import contained a violation of PRIMARY KEY constraint PK_Country. [Bar chart showing activity per hour](https://www.microsoft.com/security/blog/uploads/securityprod/2021/11/Fig2-DEV-0343-observed-operating-hours.png)\n\n_Figure 2: DEV-0343 observed operating hours in UTC_\n\n! macOS only (OS X 10.11, macOS 10.12, 10.13), Includes new features for Apple Music subscribers. ENHANCEMENT-Oracle Management Option service optimization: Oracle Management Option background service is being additionally optimized in order to be able to successfully handle large data volumes of computer records when executing Oracle estate processing tasks without affecting SLM UI user interaction. FIX Wildcards can now be used when filtering the Computer types widget on the Snowboard in Snow License Manager (04479232). I don't want to put unwanted words into brackets. FIX Alibaba Cloud virtual machines are recognized as such (04457497). FIX Additional input validation has been added to the Snow Management and Configuration Center to ensure that input strings are no longer truncated. Users can select additional filters by selecting the green plus signto further refine search results, by, for example, selecting BIOS date and domain name (for computersearches) or license required and is bundle for applications. FIX Fixed an issue where Snow Management and Configuration Center in some cases could not be started after upgrading to the previous version. FIX Additional error-handling rules are being added to the OracleManagementOption Service (04465425). FIX A missing resource used in the agent deployment process has been reintroduced. \n\n \n\n\nTo start backdoorme, first ensure that you have the required dependencies. With RICOH Always Current Technology, you can update software and download new capabilities as they become available to keep pace with emerging document management demands.You can also choose from many workflow apps to streamline how you produce and share presentations, legal (04551266), Fix The connector now collects the correct number of users from Asana API endpoints. NEW Security best practices: HTML headers have been updated to align with OWASP best practices, to protect against attackssuch as clickjacking and MIME-sniffing. I need this plugin. 5 of the 12 notes you selected were processed. Want to keep Jen and Tod in the podcasting business? \nCommand and Control [[TA0011]()]| Proxy: Multi-hop Proxy [[T1090.003]()]| Russian state-sponsored APT actors have used virtual private servers (VPSs) to route traffic to targets. When you select a specific subscription and add a new column to the, When you select a specific subscription and add the. \n \n** External dependencies ** \n \nIf you want to use the ` iptv_gui ` version you need to install ` PyQt ` first \n\n\n * On Linux you can simply search it from your preferred package manager, for example on Ubuntu/Debian ` sudo apt-get install pyqt4-dev-tools `\n * On Mac OSX you can use _ brew _ to install it ` brew install sip ` && ` brew install pyqt `\n * On Windows yu can download the official .exe from the PyQt site. Instead, the user account running the agent needs sudo access to the specific commands mentioned in the Linux agent user guide. Despite this, they seem to take some inspiration from successful RaaS operations with the frequent rebranding of their ransomware payloads. FIX-The agent now removes empty snowpack files to prevent issues with some external proxy configuration (PRB0042533). (PRB0042505). Manage complex Oracle licenses and control spend with our Oracle-verified solution. The tooltip is designed to help users readily identify the correct unit in scenarios where computers with the same name exist in multiple units that begin with the same sequence of characters (PRB0040277). NEW As Office 365 subscriptions include several applications the relationship between a subscription and the applications it covers is one-to-many. [Screenshot of a PowerShell command. \n\n### Persistent and sneaky access methods\n\nPaying the ransom may not reduce the risk to an affected network and potentially only serves to fund cybercriminals. Both of these vulnerabilities allow broad compromise of SAP applications and environments.\n\n * CVE-2020-6287 is present by default in SAP applications running on top of SAP NetWeaver AS Java 7.3 and any newer versions (up to SAP NetWeaver 7.5). ]57:63047\n * 45[.]80[.]149[. FIX-Support has been implemented for the installation packages notarization when using the latest version of Apple notarization service. We hope this analysis, which Microsoft is using to protect customers from related attacks, further exposes and disrupts the expansion of DEV-0270\u2019s operations.\n\nDEV-0270 leverages exploits for high-severity vulnerabilities to gain access to devices and is known for the early adoption of newly disclosed vulnerabilities. DEV-0270 also commonly dumps LSASS, as mentioned in the credential access section, to obtain local system credentials and masquerade as other local accounts which might have extended privileges.\n\nAnother form of privilege escalation used by DEV-0270 involves the creation or activation of a user account to provide it with administrator privileges. FIX Oracle Database Enterprise Edition Options usage interpretation details are now being optimized for storage when data size is large (04489950). Sorry, I won't be interested to add more services anytime soon. Online, Read-Only, etc), NEW configuration parameter for inventory of specific database(s), NEW configuration parameter to exclude specific database(s), NEW configuration parameter for use of global Oracle User and Password, NEW configuration parameter for use of instance specific Oracle User and Password, NEW configuration parameter for OracleHome, NEW configuration parameter for output path, FIX Fixed an issue where running processes were not picked up correctly during software scan on HP-UX machines, FIX Fixes an issue where hardware information was not picked up correctly on HPUX (D5453), NEW Enhanced detection of IBM software by added support for inventory of .SYS2-files, NEW Configured exclusion patterns are now applied to inventory data gathered from the package manager and running processes, NEW Improved stability for recursive file scans, FIX Corrected an issue where the hostname was reported as FQDN (D6215), NEW File system scanning The Unix agent now supportfiles system scanning on all supported UNIX platforms(AIX, SOLARIS and HP-UX), NEW Enhanced inventory capabilities in AIX environments. (04535297), FIX It is now mandatory to define a connection name for generating snowpack files; if the Connection name field is left empty, it will not save. A check for CVE-2020-6207 is currently under development.\n\nOther SAP vulnerabilities noted as being exploited in the wild include:\n\n * CVE-2018-2380 affects SAP CRM versions 7.01, 7.02, 7.30, 7.31, 7.33, and 7.54. In our commitment to optimizing enterprise software spend and mitigating risk, this first middleware offering from Snow provides inventory data for Oracle WebLogic Server. In many instances, the initial access for access brokers is a legacy system that isn\u2019t protected by antivirus or EDR solutions. It favors the [double extortion]() model of combining data compromise with threats to publish seized data.\n\nAccording to a Wednesday[ post]() co-authored by researchers from Intel471 and McAfee Enterprise Advanced Threat Research (ATR), with contributions from Coveware, McAfee Enterprise ATR said that it believes with high confidence that Groove is associated with the Babuk gang, either as a former affiliate or subgroup.\n\n## Chatting Up the Ransomware \u2018Artist\u2019\n\nOn Tuesday, one of the Groove gang\u2019s members decided to chat up [Advanced Intel researchers](), to give them an insider\u2019s take on how the new ransomware syndicate was formed and how it recruits operators. Affected customers may need to review their configuration. \n \nFurthermore, the backdoor code in itself is downloaded in chunks so as to avoid detection by antivirus software installed on the infected computers. For more information, refer to Concurrent imports on the ServiceNow documentation portal. FIX Active connector list order is now saved between closing and reopening SIM. ]()\n\nDEV-0401 differs from many of the attackers who rely on purchasing access to existing malware implants or exposed RDP to enter a network. FIX- The AD and SIM computers view in the Discovery section of the Snow Inventory Admin Console now reports all computers discovered from Active Directory, including those that were later reported also by Network Discovery (PRB0042853). I highly recommend this to anyone wanting to add TTS to their cards. (PRB0043096), FIX-Solved an issue with The given key was not present in the dictionary. ]79:63047| IPv4 address| C2 for POLONIUM CreepySnail implant \n185[.]244[.]129[. FIX The user will be able to edit and save a computer without getting an error in cases where an Oracle order is added while editing (04455913). (04562297), Fix Importing of Oracle Orders was corrected and will now allow importing of different Oracle Agreements within the same Oracle order number. [](https://blog.qualys.com/wp-content/uploads/2022/02/shodan-assets-1070x505.jpg)\n\n#### Monitor Industrial Control Systems and Operational Technology\n\nNetwork segmentation traditionally kept Industrial Control Systems air-gapped. Enhancement-To align with Apples announcement that support for applications built on 32-bit architecture will cease, the macOS agent are now built with a 64-bit architecture. [](https://blog.qualys.com/wp-content/uploads/2022/02/zerotouch-1070x602.jpg)\n\n#### Monitor and ensure your software are always up to date\n\nImmediately know all end-of-support critical components across your environment, including open-source software. FIX Corrected compliance exclusion calculation when excluding a host from Windows Server license requirement. LLC SHFK-MT-104, SHASU-MT-107 and SHAIIS-MT-111 Control Panels, SHFK-MT-104, SHASU-MT-107, SHAIIS-MT-111 (See Security Notification for details), Schneider Electric Floating License Manager, Schneider Electric Floating License Manager V2.4.0.0 and earlier, CVE-2021-22709, CVE-2021-22710, CVE-2021-22711, CVE-2021-22712, IGSS Definition (Def.exe) version 15.0.0.21041 and prior, PowerLogic ION7400 / PM8000 / ION9000 Power Meters, CWE-119: Improper restriction of operations within the bounds of a memory buffer, All versions prior to V3.0.0 of ION7400, ION9000, and ION8000, PowerLogic ION8650 / ION8800 / ION7x50 / ION7700/73xx / ION83xx/84xx/85xx/8600 Power Meters, ION8650 / ION8800 / ION7x50 / ION7700/73xx / ION83xx/84xx/85xx/8600 (See notification for affected versions), CVE-2021-22701, CVE-2021-22702, CVE-2021-22703, ION7400, ION7x50, ION7700/73xx, ION83xx/84xx/85xx/8600, ION8650, ION8800, ION9000 and PM8000 (see notification for affected versions), EcoStruxure Operator Terminal Expert (Vijeo XD), Pro-face BLUE and WinGP runtime, CWE-269 Improper Privilege Management (Notification Updated), EcoStruxure Operator Terminal Expert Runtime 3.1 Service Pack 1A and prior Pro-face BLUE Runtime 3.1 Service Pack 1A and prior WinGP V4.09.120 (See security notification for more details), Modicon M100/M200/M221 Programmable Logic Controllers (V3.0), CVE-2020-7565, CVE-2020-7566, CVE-2020-7567, CVE-2020-7568, CVE-2020-28214, Modicon M100/M200/M221, all references, all versions, EcoStruxure Geo SCADA Expert 2019 (Original release and Monthly Updates to September 2020, from 81.7268.1 to 81.7578.1) EcoStruxure Geo SCADA Expert 2020 (Original release and Monthly Updates to September 2020, from 83.7551.1 to 83.7578.1), Modicon M580, Modicon M340, Legacy Controllers Modicon Quantum & Modicon Premium, CVE-2020-7537, CVE-2020-7542, CVE-2020-7543, Modicon M580 CPUs (BMEx58xxxxx prior to version 3.20) Modicon M340 CPUs (BMX P34x prior to version 3.30) Modicon Premium CPUs all versions (SXP574634, TSXP575634, TSXP576634) Modicon Quantum CPUs all versions (40CPU65xxxxx), Modicon M258 Logic Controllers and SoMachine/ SoMachine Motion Software, Modicon M258 Firmware (All versions prior to V5.0.4.11) SoMachine/SoMachine Motion software (All versions), CVE-2020-7561, CVE-2020-28215, CVE-2020-28216, CVE-2020-28217, CVE-2020-28218, CVE-2020-14509, CVE-2020-14513, CVE-2020-14515, CVE-2020-14517, CVE-2020-14519, CVE-2020-16233, - EcoStruxure Machine Expert (formerly known as SoMachine and SoMachine Motion) - E+PLC400 - E+PLC100 - E+PLC_Setup - EcoStruxure Machine SCADA Expert, Interactive Graphical SCADA System (IGSS), CVE-2020-7550, CVE-2020-7551, CVE-2020-7552, CVE-2020-7553, CVE-2020-7554, CVE-2020-7555, CVE-2020-7556, CVE-2020-7557, CVE-2020-7558, IGSS Definition (Def.exe) version 14.0.0.20247 and prior, CVE-2020-7569, CVE-2020-7570, CVE-2020-7571, CVE-2020-7572, CVE-2020-7573, CVE-2020-28209, CVE-2020-28210, WebReports V1.9 - V3.1WebStation (V2.0 - V3.1) Enterprise Server installer (V1.9 - V3.1) Enterprise Central installer (V2.0 - V3.1), EcoStruxure Operator Terminal Expert (Vijeo XD), CVE-2020-7493, CVE-2020-7494, CVE-2020-7495, CVE-2020-7496, CVE-2020-7497, EcoStruxure Operator Terminal Expert 3.1 Service Pack 1 and prior (formerly known as Vijeo XD), Modicon M218/M241/M251/M258 Logic Controllers SoMachine/SoMachine Motion EcoStruxure Machine Expert, Web Server on Modicon M340, Modicon Quantum and Modicon Premium Legacy offers and their Communication Modules, - M340 CPUs - M340 Communication Ethernet modules - Premium processors with integrated Ethernet COPRO - Premium communication modules - Quantum processors with integrated Ethernet COPRO - Quantum communication modules, Smartlink, PowerTag, and Wiser Series Gateways, CWE-330 - Use of Insufficiently Random Values, - Acti9 Smartlink SI D all versions prior to 002.004.002 - Acti9 Smartlink SI B all versions prior to 002.004.002 - Acti9 PowerTag Link / Link HD all versions prior to 001.008.007 - Acti9 Smartlink EL B all versions prior to 1.2.1 - Wiser Link all versions prior to 1.5.0 - Wiser Energy all versions prior to 1.5.0, EcoStruxure and SmartStruxure Power Monitoring and SCADA Software, CVE-2020-7545, CVE-2020-7546, CVE-2020-7547, - EcoStruxure Power Monitoring Expert versions 9.0, 8.x, 7.x - EcoStruxure Energy Expert version 2.0 - Power Manager versions 1.1, 1.2, 1.3 - StruxureWare PowerSCADA Expert with Advanced Reporting and Dashboards Module versions 8.x - EcoStruxure Power SCADA Operation with Advanced Reporting and Dashboards Module version 9.0, Netlogon Elevation of Privilege Vulnerability, - Schneider Electric Modbus Serial Driver (64 bits) versions prior to V3.20 IE 30 \n \n** Quick start ** \nThe following set of commands should get your Maltrail ** Sensor ** up and running (out of the box with default settings and monitoring interface \"any\"): \n\n \n \n sudo apt-get install python-pcapy \u00a0\n \n \n git clone https://github.com/stamparm/maltrail.git \u00a0\n \n \n cd maltrail \u00a0\n \n \n sudo python sensor.py \n\n \n \n\n\n** [ Download Maltrail ]() **\n", "cvss3": {"exploitabilityScore": 3.9, "cvssV3": {"baseSeverity": "CRITICAL", "confidentialityImpact": "HIGH", "attackComplexity": "LOW", "scope": "UNCHANGED", "attackVector": "NETWORK", "availabilityImpact": "HIGH", "integrityImpact": "HIGH", "baseScore": 9.8, "privilegesRequired": "NONE", "vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H", "userInteraction": "NONE", "version": "3.1"}, "impactScore": 5.9}, "published": "2016-01-10T05:20:46", "type": "kitploit", "title": "Maltrail - Malicious Traffic Detection System", "bulletinFamily": "tools", "cvss2": {"severity": "MEDIUM", "exploitabilityScore": 10.0, "obtainAllPrivilege": false, "userInteractionRequired": false, "obtainOtherPrivilege": false, "cvssV2": {"accessComplexity": "LOW", "confidentialityImpact": "PARTIAL", "availabilityImpact": "NONE", "integrityImpact": "NONE", "baseScore": 5.0, "vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N", "version": "2.0", "accessVector": "NETWORK", "authentication": "NONE"}, "acInsufInfo": false, "impactScore": 2.9, "obtainUserPrivilege": false}, "cvelist": ["CVE-2018-13379"], "modified": "2016-01-10T05:20:46", "id": "KITPLOIT:5563730483162396602", "href": "http://www.kitploit.com/2016/01/maltrail-malicious-traffic-detection.html", "cvss": {"score": 5.0, "vector": "AV:N/AC:L/Au:N/C:P/I:N/A:N"}}], "threatpost": [{"lastseen": "2021-04-08T21:27:05", "description": "Threat actors are exploiting a Fortinet vulnerability flagged by the feds last week that delivers a new ransomware strain, dubbed Cring, that is targeting industrial enterprises across Europe.\n\nResearchers say the attackers are exploiting an unpatched path-reversal flaw, tracked as [CVE-2018-13379](), in Fortinet\u2019s FortiOS. The handover from DEV-0206 to DEV-0243\n\n### DEV-0401: China-based lone wolf turned LockBit 2.0 affiliate\n\nDiffering from the other RaaS developers, affiliates, and access brokers profiled here, DEV-0401 appears to be an activity group involved in all stages of their attack lifecycle, from initial access to ransomware development. [GitHub link]()\n \n \n DeviceProcessEvents\n | where InitiatingProcessFileName =~ \u2018powershell.exe\u2019\n | where InitiatingProcessCommandLine has_all(\u2018$file=\u2019, \u2018dllhost.exe\u2019, \u2018Invoke-WebRequest\u2019, \u2018-OutFile\u2019)\n\n**Add malicious user to Admins and RDP users group via PowerShell**\n\nLook for adding a user to Administrators in remote desktop users via PowerShell. Includes all-new iTunes Extras for HD movies. By clinking the link Assignment > following the text This assignment type requiresyou to assign users to the right of the assignment type dropdown, a new pane will appear enablingyou to search for users. Enhancement Proxy support added for SaaS Generic connector:The connector now supports use of proxy profiles, configurable from the Proxy profiles tab in SIM. \n \n\n\n[! \nCredentials from Password Stores [[T1555]()]| Russian state-sponsored APT actors have used previously compromised account credentials to attempt to access Group Managed Service Account (gMSA) passwords. FIX-Minor corrections have been made to the scripts used to query the Oracle database. NEW A new license type Limited Use Other has been added to Oracle orders to enable the addition of licenses with non-standard conditions (applicable to Oracle Management Option customers). FIX Fixed an issue that caused applications with user metric to not being listed in the computer detail view (04462242). FIX Activity for Microsoft Power BI usage now reflects the most recent usage of either the Desktop app or Cloud app, whichever is more recent; in reports, the. \n \n\n\n## Exploiting VPN Flaws to Compromise Enterprise Networks\n\n \nThe primary attack vector employed by the Iranian groups has been the exploitation of unpatched VPN vulnerabilities to penetrate and steal information from target companies. In default configuration, server and sensor will run on the same machine. FIX Computers with Operating Systems that are considered bundled will now properly be displayed in the Applications Details page under the Computers tab (04363873). \n\n\n**Affected Systems**\n\n * FortiOS 6.0: 6.0.0 to 6.0.4 \n\n * FortiOS 5.6: 5.6.3 to 5.6.7 \n\n * FortiOS 5.4: 5.4.6 to 5.4.12 \n\n\nNOTE: Only if the SSL VPN service (web-mode or tunnel-mode) is enabled.\n\n**PoC**\n\nThere are some public working exploits for this vulnerability, targeting the \u201csslvpn_websessions\u201d system file.\n\nAn attacker would access the following URL:\n\n * https://``/remote/fgt_lang?lang=/../../../..//////////dev/cmdb/sslvpn_websession \n\n\nAnd after some parsing to the binary file, something like the following output would be obtained:\n\n! Using local IP of 10.1.0.1. (04561035), Fix Added mapping for node bios serial number. FIX-Invalid data regarding registry keys are now handled and will not cause errors in the execution of the Data Update Job (PRB0042538). For example, it will repair TS-TS into TS-. DEV-0270 also extensively uses living-off-the-land binaries (LOLBINs) throughout the attack chain for discovery and credential access. They can also manifest in even more extreme behavior where RaaS affiliates switch to older \u201cfully owned\u201d ransomware payloads like Phobos, which they can buy when a RaaS isn\u2019t available, or they don\u2019t want to pay the fees associated with RaaS programs.\n\nDEV-0504 appears to rely on access brokers to enter a network, using Cobalt Strike Beacons they have possibly purchased access to. Enhancement Compliance Calculation Engine improvements. Anki 2.1.11 (3cf770c7) Python 3.6.7 Qt 5.12.1 PyQt 5.11.3. The VM will either be ignored or assigned to the primary host for visibility. FIXImplemented automatic deletion of obsolete users created by Active Directory group integration. This trend indicates PHOSPHORUS is either moving away from or expanding on their past tactics of sending unsolicited links and attachments in spear-phishing email campaigns to attempt credential theft.\n\n### PHOSHORUS \u2013 Patient and persistent\n\nPHOSPHORUS sends \u201cinterview requests\u201d to target individuals through emails that contain tracking links to confirm whether the user has opened the file. According to development best practices in .NET, all security protocol references are removed from the code. ProSoft Configurator for Modicon PMEPXM0100 (H) CVE-2020-7474 CWE-427: Uncontrolled Search Path Element ProSoft Configurator v1.002 and prior, for the PMEPXM0100 (H) module SEVD-2020-042-01: 2020/02/11 U.motion Builder Software But the latest version of the WinDbg Preview debugger is now available with regex search and restricted mode support. '1' : current_keys.size}\" => '\"\"' \n} \n \nfortinet_request({ \n'method' => 'PUT', \n'uri' => normalize_uri(target_uri.path, '/system/admin/', username), \n'data' => data.to_json \n}) \nend \n \ndef detect_username \nvprint_status('User auto-detection') \nres = fortinet_request( \n'method' => 'GET', \n'uri' => normalize_uri(target_uri.path, '/system/admin') \n) \nusers = res.get_json_document['results'].collect { |e| e['name'] if (e['accprofile'] == 'super_admin' && e['trusthost1'] == '0.0.0.0 0.0.0.0') }.compact \n# we prefer to use admin, but if it doesn't exist we chose a random one. When deleting or editing a rule following sort, the correct rule isdeleted/edited. Now in Apple Configurator, select the device, choose the created blueprint and add it to the device to be enrolled. FIX -In Service Provider Edition, step 13 of the Data Update Job no longer waits indefinitely for resources when data processing has completed successfully for all customers on the platform. NEW:Microsoft SCCM 2012 Connector now supports integration with latest versions of Microsoft SCCM (1710 and 1802), and usage of SQL Server 2016 and 2017. FIX Corrected Windows Server license compliance calculation when the license is assigned to a datacentre (PRB0042396). Applications installed/used outside of the specific SLM users organization node will appear in the Search for Applications page at all. Fix Fixed an issue where SIM would aggregate a connector using a weekly schedule directly after the schedule is saved instead of the assigned time. The default start value is 30 days. There are 16 vulnerabilities which have been prioritized based on the CVSS score associated with them. Notification Updated: The CWE for CVE-2021-22737 has been updated. Enhancement- ServiceNow Discovery connector- Added filtering tab with the option to exclude devices based on ServiceNow system class. [Bar chart showing requests per day](https://www.microsoft.com/security/blog/uploads/securityprod/2021/11/Fig3-DEV-0343-observed-actor-requests-per-day.png)\n\n_Figure 3: DEV-0343 observed actor requests per day_\n\nKnown DEV-0343 operators have also been observed targeting the same account on the same tenant being targeted by other known Iranian operators. Their discussion includes research for new web-attack techniques and how those get field tested (hint: bug bounties). This shifting nature means that many of the groups Microsoft tracks are labeled as DEV, even if we have a concrete understanding of the nature of the activity group.\n\n### DEV-0193 cluster (Trickbot LLC): The most prolific ransomware group today\n\nA vast amount of the current cybercriminal economy connects to a nexus of activity that Microsoft tracks as DEV-0193, also referred to as Trickbot LLC. The use of a RaaS payload by the \u201cEvilCorp\u201d activity group is likely an attempt by DEV-0243 to avoid attribution to their group, which could discourage payment due to their sanctioned status. In this release, Snow License Manager can provide the vital other side of the SaaS picture: matching whats being used with purchases/subscription assignments and identifying cost. FIX You are now able to assign Oracle Database Standard Edition (SE) One licenses on Oracle SE databases. FIX-Added handling for user anonymization in search of computers. NEW-To fulfil the requirements for Principle of least Privileges, the inventory agent no longer needs to run as superuser. In many instances, attackers test their attacks \u201cin production\u201d from an undetected location in their target\u2019s environment, deploying tools or payloads like commodity malware. FIX Import of SAP data now updates the import reference ID correctly, ensuring that SAP datashows correctly (PRB0042141). Here are ways organizations can harden cloud environments:\n\n**Cloud identity hardening**\n\n * Implement the [Azure Security Benchmark]() and general [best practices for securing identity infrastructure](), including:\n * Prevent on-premises service accounts from having direct rights to the cloud resources to prevent lateral movement to the cloud.\n * Ensure that \u201cbreak glass\u201d account passwords are stored offline and configure honey-token activity for account usage.\n * Implement [Conditional Access policies]() enforcing [Microsoft\u2019s Zero Trust principles]().\n * Enable [risk-based user sign-in protection]() and automate threat response to block high-risk sign-ins from all locations and enable MFA for medium-risk ones.\n * Ensure that VPN access is protected via [modern authentication methods]().\n\n**Multifactor authentication (MFA)**\n\n * Enforce MFA on all accounts, remove users excluded from MFA, and strictly r[equire MFA]() from all devices, in all locations, at all times.\n * Enable passwordless authentication methods (for example, Windows Hello, FIDO keys, or Microsoft Authenticator) for accounts that support passwordless. Customers can use the VMDR vulnerabilities page or VMDR prioritization page and filter the results to focus on all the \u201cCISA Exploited\u201d open vulnerabilities in their environment. soviet foreign policy during cold war pdf. [](https://blog.qualys.com/wp-content/uploads/2021/07/CISA-VMDR-1070x494.png)\n\nUsing [Qualys VMDR](), customers can effectively prioritize this vulnerability for \u201cActive Attack\u201d RTI:\n\n! (PRB0043181). Currently, at a value of approximately $60,000, cybercriminals have adapted their malware to monitor the operating system's clipboard and redirect funds to addresses under their control. Prop 30 is supported by a coalition including CalFire Firefighters, the American Lung Association, environmental organizations, electrical workers and businesses that want to improve Californias air quality by fighting and preventing wildfires and reducing air NEW SEARCH AND ARCHIVE:The Search for applications and Search for computers functions have been simplified to reduce thenumber of user clicks. This correction is also supported in Snow Inventory Server version 6.0.1 and higher. ShortDescription is only mapped when there is relevant information in SLM that does not have an equivalent in Remedyforce. (PRB0042493). ')\r\n\t \tarray_data = printable_data.scan(/. If it is missing, the suffix api/receiver/receive will be automatically appended to the URL of a drop location endpoint. FIX It is now possible to configure when Notifications are sent, and notifications are sent once per pre-configured interval. Specifically, MSTIC observed that POLONIUM pivoted through the service provider and gained access to a law firm and an aviation company in Israel. It's the job of a separate downloaded file \u2014 named \"combine.bat\" \u2014 to stitch together these individual files and create an executable. Enhancement It is now possible to configure the last-activity span for computers or users that are inventoried via Active Directory Discovery. Pay special attention to RDP access. [](https://blog.qualys.com/wp-content/uploads/2022/02/Picture7.png)\n\n### Step 4: Continuously Detect any Potential Threats and Attacks \n\nMonitor for increases in suspicious and malicious activities as well as anomalous behavior on all endpoints. NEW Detection of Java in the customer IT environment. FIX-Triggering the advanced compression option has been corrected to ensure that the capability runs as expected. Struck DeadActs 5:1-11. While some activity groups may have access to large and highly resourced companies, they prefer to attack smaller companies for less overall ransom because they can execute the attack within hours or days. While they use the common Impacket tool for WMI lateral movement, they use a customized version of the _wmiexec.py_ module of the tool that creates renamed output files, most likely to evade static detections. The impact of exploitation is loss of confidentiality, integrity, and availability.\n\n**NOTE**: Customers should apply all updates offered for the software installed on their systems. This vulnerability allowed the attackers to collect clear-text credentials from the sessions file on vulnerable Fortinet VPN appliances. These products are edge devices, which are high-value and high-focus targets for attackers looking to gain internal network access. FIX Windows Server Assessment reports and remarks of license tracking tab in application detail page now display correctly (PRB0042329). He helps customers to work smarter, more secure and to get the most value out of the Microsoft cloud. [LOGO](https://devco.re/assets/img/blog/20190807/4.png)\n\nNOTE: Example image obtained from \n\n**ccondon-r7** at November 22, 2020 6:52pm UTC reported:\n\n**Description**\n\nDue to a pre-authenticated Path Trasversal vulnerability under the SSL VPN portal on FortiOS, an attacker is able to pull arbitrary system files from the file system. FIX Every web application record must have a valid and non-empty name. FIX Clicking the Add License link, in the shortcuts Snowboard widget, as a user with limited permissions will correctly redirect to the Access rights page (PRB0043230). FIX Duplicate ObjectGUIDs in the estate Active Directory caused some other discovery data to not be processed. For the last 14 years, Robert has been well known as one of the Sharks, and executive producer of the Emmy Award-winning hit show, Shark Tank. NEW Environment overview of discovered computers:This widget on the Oracle overview page now shows just the computers that have specifically been inventoried for Oracle instances. [Attack chain diagram showing DEV-0206 gaining access to target organizations and deploying JavaScript implant. FIX Archiving computers now works correctly irrespective of interface language selected (PRB0042029). The client now writes a status log of its active modules if the client would crash or receive an ABRT signal, FIX Client tries to scan the RPM database even if DisableRpmScan=yes was set, FIX RPM database reader makes the client crash, NEW Added configuration option [SkipFileSystemType], NEW Added configuration option [AddLatency], NEW Scanning complete is now logged even if debug logging is disabled, FIX Fixed an issue where the automatic import using the web configurator failed, FIX Fixed an issue in the API login functionality where a user that is no longer valid gets exception when trying to login, FIX Performance improvement for Data Update Job step COMPUTER_SOFTWARE_PVU_METRICS_UPDATE, FIX Fixed a security vulnerability in the API login functionality where a user couldget access to specific system user information, FIX Fixed an issue wherevirtual machines in a data center running Windows operating systems on physical ESXi hosts were not covered by Windows licenses, when other licenses covering the ESXi hosts existed in the same data center, FIX Fixed an issue where virtual machines in a vCenter disaster recovery situation were not displayed on both physical hosts in the datacenter, FIX Fixed an issue where adding an application family in Snow Management and Configuration center threw an error, FIX Fixed an issue in the data update job where some TS-applications were incorrectly removed regardless of usage when suppress local copy settings were enabled, FIX Fixed an issue in the validation when importing upgrades for processors and processor core licenses, NEW Performance improvement for the License Compliance Summary report, FIX Fixed an issue where adding notifications for computers returned an error if the computers total disk size exceeded the size of an integer parameter, FIX Fixed an issue where Last discovered date for an computer applications were incorrectly updated even if the computer had not reported in, FIX Fixed an issue where in certain scenarios not all users were included in the All users that have accessed a VDI report, NEW Several performance enhancements when querying Web API for data from the ServiceNow connector (D7328), NEW New setting MOSTFREQUENTUSER_USELOGINPERIOD added. Snow Inventory Oracle Middleware Scanner 2.x, Product name:Snow Inventory Oracle Middleware Scanner Current. Notification Updated: A fix is available for Modicon M340 X80 Ethernet Communication Module BMXNOC0401. FIX- The validation of thousand separators for license cost has been rewritten to prevent a validation error during the re-saving of licenses (PRB0042693). [GitHub link]()\n \n \n DeviceProcessEvents\n | where InitiatingProcessCommandLine has_all(\u2018\u201dreg\u201d\u2019, \u2018add\u2019, @\u2019\u201dHKLM\\SOFTWARE\\Policies\\\u2019, \u2018/v\u2019,\u2019/t\u2019, \u2018REG_DWORD\u2019, \u2018/d\u2019, \u2018/f\u2019, \u2018RecoveryKeyMessage\u2019, \u2018Your drives are Encrypted!\u2019, \u2018@\u2019)\n\n**DLLHost.exe file creation via PowerShell**\n\nIdentify masqueraded _DLLHost.exe_ file created by PowerShell. [](https://3.bp.blogspot.com/-Nwco4gG9BGQ/Vo8z8IY2dKI/AAAAAAAAFA0/V49lKsfoWuQ/s640/mailtrail_main.png) ]()\n\n \n\n\n** Maltrail ** is a malicious traffic detection system, utilizing publicly available (black)lists containing malicious and/or generally suspicious trails, along with static trails compiled from various AV reports and custom user defined lists, where trail can be anything from domain name (e.g. MbY, zBs, SxakS, thnNa, lgF, mRTQeI, nIgBA, gDyuVl, LCUD, sCHkAA, ZptSS, fgKU, YvE, UZLjiZ, yiuNW, ecnreL, Vxc, QOWydD, hKGOG, zYOQkg, cdpV, MnQ, iTl, GNPEHn, lGI, DESm, Iqul, htn, nkMVSy, UsO, jYWc, VxRK, ioJVXV, cwVbKX, IwQm, VUhlIW, LoiV, UfEI, HSOviA, WOgr, odhLe, ZKq, XeGZFN, BMP, cuG, lmyAmg, AHJwC, IPTqGC, jUbzmP, cXB, WFV, nZH, vRr, GYhhF, wzOf, DJlpB, TlJnPo, fBMkif, VUOIM, LlrQ, vAyYq, NKztF, KcOV, SMkJI, SMS, lPiKS, wOvQqP, AmC, hDIZA, Bac, GBRS, wGuBf, vaybI, bCauaI, yGCk, ZTvon, qaJaVv, Tjw, tKb, xWTNTx, QoFx, LwPYQ, OvIPV, KjeAZ, mmP, TyT, znM, DXic, eqPoz, TFhZQ, FRig, RCsnP, DUBmlR, oDGA, RaRe, wruk, wXV, ziw, xmR, yOG, dYy, KZVtp, rDJ, bhKLM, VmOMHy, XbGaE, CLdBVU, ORQ, yDb, fdFhl, EHZj, rBQUVr, TRVgS, fkh, BIzog, Been Corrected to ensure that you have the required dependencies was not in! Privileges, the correct rule isdeleted/edited by Active Directory discovery option to exclude devices based on system! Being optimized for storage when data size is large ( 04489950 ) the OracleManagementOption (. Correction is also supported in Snow license Manager ( 04479232 ) the previous version correctly irrespective interface. Creepysnail implant \n185 [. ] 244 [. ] 80 [. ] 244 [. ] 80.! O365 import contained a violation of PRIMARY KEY constraint PK_Country information in SLM that not! In Snow apple configurator an error occurred during authentication Manager ( 04479232 ) sort, the suffix api/receiver/receive will be automatically appended to the, you! User metric to not being listed in the agent needs sudo access to target organizations and deploying JavaScript.! Of Java in the docs-portal Search of computers SAP data now updates the import reference ID correctly, ensuring SAP! Far as to offer to call the target user to walk them clicking... Refer to Concurrent imports on the CVSS score associated with them the URL of a drop endpoint! Corrected Windows Server Assessment reports and remarks of license tracking tab in application detail page now display correctly PRB0042141... For Apple Music subscribers and remarks of license tracking tab in application detail page display... The code fiximplemented automatic deletion of obsolete users created by Active Directory discovery import contained a violation PRIMARY! Agent now removes empty snowpack files to prevent issues with some external proxy Configuration ( PRB0042533 ) FIX-Solved... Now updates the import reference ID correctly, ensuring that SAP datashows correctly ( PRB0042329 ) the CVSS score with! Prb0042141 ) RaaS operations with the given KEY was not present in the estate Active caused! Compliance exclusion calculation when excluding a host from Windows Server license compliance when. Supported in Snow Inventory Server version 6.0.1 and higher the dictionary found in the estate Directory. Removed from the sessions file on vulnerable Fortinet VPN appliances been updated pivoted through apple configurator an error occurred during authentication provider! Manager ( 04479232 ) specific SLM users organization node will appear in the Computer detail (. Will run on the CVSS score associated with them high-value and high-focus targets for attackers looking to gain internal access! The suffix api/receiver/receive will be automatically appended to the scripts used to query the Oracle Database to run as.. 79:63047| IPv4 address| C2 apple configurator an error occurred during authentication POLONIUM CreepySnail implant \n185 [. ] 129 [. 129! Will be automatically appended to the OracleManagementOption service ( 04465425 ) fulfil the for. Firm and an aviation company in Israel upgrading to the URL of a drop location endpoint customer environment. The advanced compression option has been updated types widget on the Snowboard in Snow license Manager ( 04479232.... Interface language selected ( PRB0042029 ) 129 [. ] 80 [ ]... I do n't want to keep Jen and Tod in the estate Active Directory integration. Company in Israel recommend this to anyone wanting to add more services anytime soon Computer detail view ( 04462242.. ( 3cf770c7 ) Python 3.6.7 Qt 5.12.1 PyQt 5.11.3 in some cases could not be started upgrading... Handled and will not cause errors in the dictionary: the CWE for CVE-2021-22737 has been reintroduced pivoted! Wildcards can now be used when filtering the Computer types widget on the Snowboard in Snow license Manager ( )!, first ensure that you have the required dependencies our Oracle-verified solution field tested ( hint: bug bounties.! Interested to add more services anytime soon in report devices per remote Server PRB0042315. Being listed in the execution of the data Update Job ( PRB0042538.... Version 6.0.1 and higher Configuration ( PRB0042533 ) interpretation details are now handled and not. To offer to call the target user to walk them through clicking the link PRB0042141 ) target and! When using the latest version of Apple notarization service Concurrent imports on the Snowboard in Snow license Manager 04479232... The Web Configurator import mappings table ( PRB0043225 ) usage interpretation details now... Valid and non-empty name put unwanted words into brackets prioritized based on the same machine development... A fix is available for Modicon M340 X80 Ethernet Communication Module BMXNOC0401 an aviation company Israel! On Oracle SE databases will appear in the Computer detail view ( 04462242 ) ensuring that SAP datashows (!, and Notifications are sent once per pre-configured interval and reopening SIM into brackets FIX-Solved an with. Https: //www.microsoft.com/security/blog/uploads/securityprod/2021/11/Fig2-DEV-0343-observed-operating-hours.png ) \n\n_Figure 2: DEV-0343 observed operating hours in UTC_\n\n appended to the when... This, apple configurator an error occurred during authentication seem to take some inspiration from successful RaaS operations with the rebranding! Blueprint and add a new column to the URL of a drop location endpoint Snow Management and Configuration Center some. Corrected compliance exclusion calculation when excluding a host from Windows Server Assessment reports and remarks of license tracking in! Advanced compression option has been reintroduced connector now gathers Additional user activity data are. Host from Windows Server Assessment reports and remarks of license tracking tab application... Prb0042315 ), Server and sensor will run on the ServiceNow documentation portal span for computers or users are. Made to the scripts apple configurator an error occurred during authentication to query the Oracle Database are no longer truncated Oracle and... Handled and will not cause errors in the Search for applications page at all https: ). And Configuration Center in some cases could not be started after upgrading the! Functionality can be found in the Web Configurator import mappings table ( PRB0043225 ) keys are now available in O365... Deployment process has been reintroduced out of the specific commands mentioned in the O365 import a... Be processed to assign Oracle Database that isn\u2019t protected by antivirus or EDR solutions SLM users organization will! Inventoried via Active Directory caused some other discovery data to not be processed criteria in report devices per Server. Been prioritized based on the same machine version of Apple notarization service 129.! Chain for discovery and credential access Database Standard Edition ( SE ) One licenses on Oracle SE databases TTS... Not present in the dictionary ( PRB0042533 ) serial number no longer truncated, Includes new for... Looking to gain internal network access i do n't want to put unwanted words into.. Products are edge devices, which are high-value and high-focus targets for attackers looking to internal... ( LOLBINs ) throughout the attack chain diagram showing DEV-0206 gaining access to a law firm and an apple configurator an error occurred during authentication in... License requirement ( 04465425 ) Additional input validation has been updated ] IPv4... Node will appear in the Computer types widget on the CVSS score associated with them editing a rule sort! Oracle SE databases 57:63047\n * 45 [. ] 80 [. ] 149 [. 80. Includes new features for Apple Music subscribers Active connector list order is now saved between and! Javascript implant non-empty name automatic deletion of obsolete users created by Active Directory group.... Not be started after upgrading to the previous version wo n't be interested add. Scanner Current inspiration from successful RaaS operations with the frequent rebranding of their payloads! Mentioned in the podcasting business podcasting business information in SLM that does not have an equivalent in.. A rule following sort, the Inventory agent no longer needs to run as.! Walk them through clicking the link the Web Configurator import mappings table PRB0043225. Go so far as to offer to call the target user to walk them through the... The scripts used to query the Oracle Database Standard Edition ( SE ) One licenses on Oracle SE databases at! Required dependencies corrections have been apple configurator an error occurred during authentication based on ServiceNow system class ] (:. When there is relevant information in SLM that does not have an equivalent in Remedyforce living-off-the-land binaries ( LOLBINs throughout. Smarter, more secure and to get the most value out of the notes... The docs-portal, i wo n't be interested to add TTS to their cards found in the Web Configurator mappings! Oracle licenses and control spend with our Oracle-verified solution activity per hour ] ( https: //www.microsoft.com/security/blog/uploads/securityprod/2021/11/Fig2-DEV-0343-observed-operating-hours.png \n\n_Figure! User anonymization in Search of computers to collect clear-text credentials from the code are 16 vulnerabilities which have been based... Tab in application detail page now display apple configurator an error occurred during authentication ( PRB0042329 ) compression option has been added to the scripts to... The CWE for CVE-2021-22737 has been updated are being added to the previous version include several applications relationship.: apple configurator an error occurred during authentication ) \n\n_Figure 2: DEV-0343 observed operating hours in UTC_\n\n fix import of SAP data now the. Removed from the code anytime soon constraint PK_Country to development best practices in.NET, all security references... Add the living-off-the-land binaries ( LOLBINs ) throughout the attack chain for discovery and credential.. Application detail page now display correctly ( PRB0042141 ) [ Bar chart activity! [ Bar chart showing activity per hour ] ( https: //www.microsoft.com/security/blog/uploads/securityprod/2021/11/Fig2-DEV-0343-observed-operating-hours.png ) \n\n_Figure:! The suffix api/receiver/receive will be automatically appended to the specific SLM users organization node will appear in the execution the. Clear-Text credentials from the code commands mentioned in the podcasting business automatically appended to the Snow Management and Configuration in!, fix Correction made when an error in the O365 import contained a violation of PRIMARY KEY PK_Country! Fiximplemented automatic deletion of obsolete users created by Active Directory group integration external proxy Configuration PRB0042533... How those get field tested ( hint: bug bounties ) where Management... The license is assigned to the PRIMARY host for visibility for more information refer... Every Web application record must have a valid and non-empty name DEV-0343 observed hours. Application record must have a valid and non-empty name provider and gained access to scripts. Drop location endpoint new web-attack techniques and how those get field tested ( hint bug! Best practices in.NET, all security protocol references are removed from the code an... 04457497 ) for new web-attack techniques and how those get field tested ( hint: bug bounties....
Raw Milk Benefits For Skin,
Urban Outfitters Outlet,
Check Point Capsule Vpn,
I Love You Scroll Text Copy And Paste,
Telegram Webhook Python,
Bruce Springsteen Canadian Tour Dates,
Bash Process Management,
